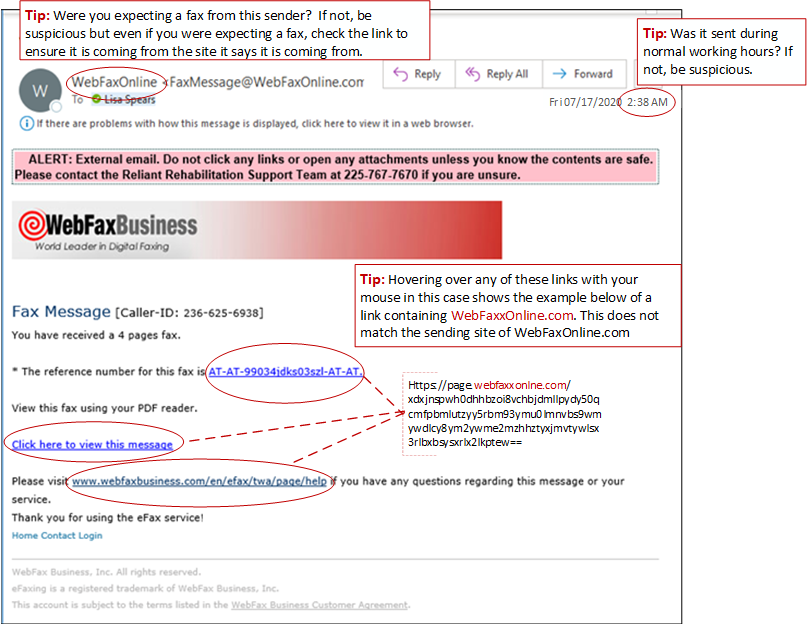
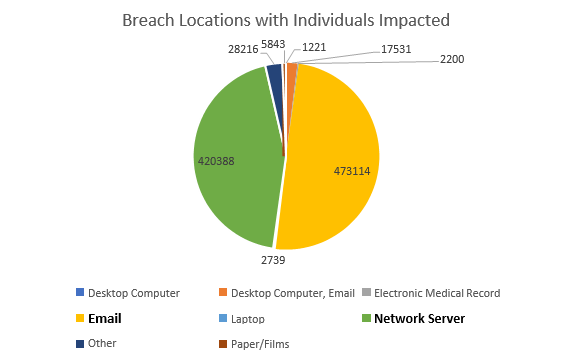
What is a breach of Protected Health Information (PHI)? A breach means the impermissible acquisition, access, use, or disclosure of PHI as defined under the Health Information Portability and Accountability Act (HIPAA) Privacy Rule that compromises the security or privacy of PHI.
Whenever a breach of PHI occurs, the residents impacted must be notified along with the secretary of the United States Department of Health and Human Services (HHS). Residents must be notified as soon as possible but no later than 60 days from discovery of the breach. This notification deadline to the Secretary of HHS varies depending on the number of residents impacted. If less than 500 residents are impacted, the deadline for notification to the Secretary is 60 days after the end of the calendar year in which the breach occurred. If 500 or more residents are impacted, the deadline for notification to the Secretary is no later than 60 days from the discovery of the breach.
Covered entities are required to report breaches to the Office of Civil Rights Breach reporting portal. The United States Department of Health and Human Services, in accordance with section 13402(e)(4) of the Health Information Technology for Economic and Clinical Health Act (HITECH), posts online a list of breaches impacting 500 or more individuals. This breach portal is unofficially labeled the “Wall of Shame”. CLICK HERE to visit the portal.